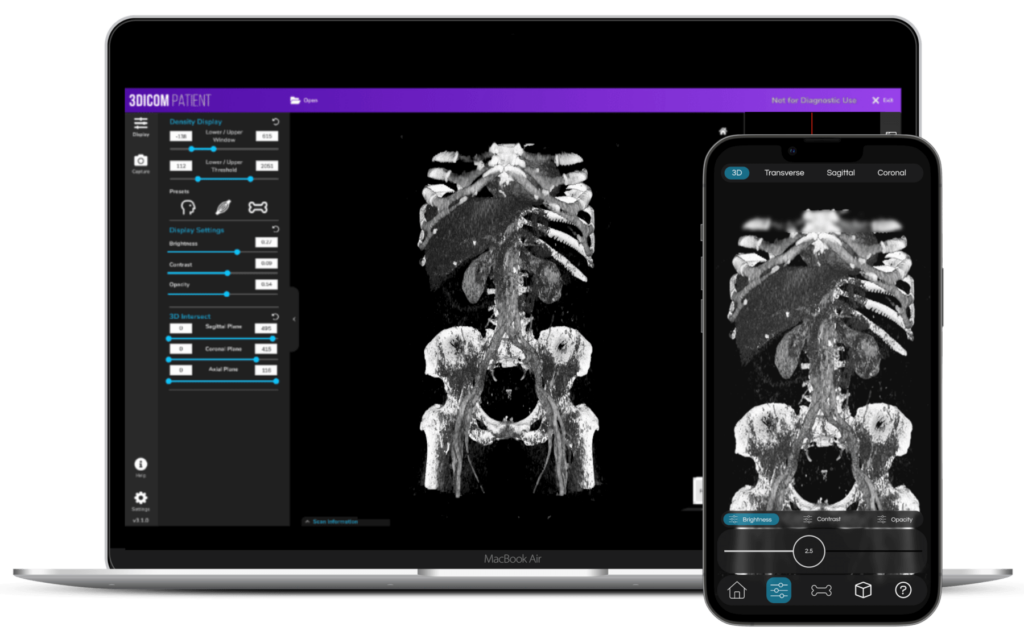
Finding a reliable iOS DICOM viewer to access medical images on the go can be challenging.
With protected health information (PHI) involved, it’s crucial to select an app with robust security and compliance protections.
This guide covers key factors to evaluate when choosing a DICOM viewer iOS to safeguard your data.
The Risks of Consumer DICOM Viewers
With healthcare mobility accelerating, the app stores offer numerous consumer-grade DICOM viewers for iOS devices.
However, most fail to provide adequate confidentiality, integrity, and access controls for sensitive DICOM data.
Consumer viewers lack measures like:
- Authentication protocols beyond basic passwords
- Granular user permissions and access limits
- Configurable security policies to harden the app
- Audit logging to track data use
- HIPAA compliance frameworks
Without proper safeguards, breaches and unauthorized access can jeopardize patients and providers alike.
Vetting Developer Credibility
The quality and security of a DICOM app depend heavily on the developer. When researching options:
- Scrutinize the Developer’s Background – Do they have extensive healthcare IT experience and proven security capabilities? An established track record instills confidence.
- Verify HIPAA Validation – Have they undergone third-party auditing to validate HIPAA compliance processes? Look for HITRUST certification or similar credible verification.
- Ask About Development Practices – What measures do they take to ensure security by design and prevent vulnerabilities? Rigorous testing and code review processes are essential.
- Check Client References – Ask for healthcare clients you can contact to discuss their experiences with the product and vendor. The most credible developers will readily provide references.
Required Technical Safeguards
A secure healthcare DICOM viewer app should incorporate:
- Encrypted Local Storage – Data at rest on the device must utilize AES or equivalent strong encryption to prevent unauthorized access if the device is lost or stolen.
- Secure Data Transmission – All network communication and DICOM transfer must be encrypted through current protocols like TLS or VPN. Outdated SSL is inadequate.
- Granular Access Policies – To limit data visibility, Configure stringent access rules based on user role, IP address range, etc.
- Configurable Authentication – Support various login methods, such as passwords, biometrics, smart cards, or SSO, to authorize users.
- Remote Wipe Capability – Ability to remotely wipe PHI from lost mobile devices.
Key Features for Protection and Compliance
Look for built-in capabilities to manage and safeguard data:
Access Auditing
Detailed logging of user activity provides visibility into data access. Alerts flag suspicious activity.
Anonymization Tools
De-identify PHI by removing or masking patient details in images. Critical for sharing beyond care teams.
Data Loss Prevention
Restrict saving, printing, and sharing functions. Prevent photographs or screenshots.
Permissions Flexibility
Fine-tune user and group permissions for specific data access needs while limiting visibility.
Disconnected Support
Cache and synchronize data to provide availability during network dips.
Handling App Updates and OS Upgrades
With Apple’s frequent iOS updates, make sure the developer is committed to maintaining compatibility through:
- Regular app updates in pace with iOS changes
- Rigorous app testing against iOS beta releases
- Proactive user communication around required updates and changes
A lack of currency can render apps unusable. Avoid developers with slow update cycles.
Organizational App Management
For enterprise-wide secure deployment, look for:
- Volume licensing options
- Integration with the existing identity provider (IdP) for single sign-on
- App configuration and policies pushed from a central mobile device management (MDM) system
- Ability to remotely disable access or wipe the app if the device is lost/stolen
Centralized controls amplify security and simplify accessing DICOM data from mobile iOS devices, even at a large scale.
Healthcare mobility demands balancing ubiquitous access with ironclad PHI protections. Using the criteria above, you can confidently select an iOS DICOM viewer that meets your data security imperatives. Look beyond basic functionality to how the app safeguards your patients, providers, and organization.